Ransomware-proof data storage
Ransomware attacks are an increasing threat to the availability of data within organizations. The threat is not reserved for a particular industry or type of organization, anyone can be affected. As shown in the figures below, it is not just a single threat, but there are many. And it doesn’t matter if you use an on-premise or a cloud solution
Of course, it remains important to remind end-users of the danger of these types of crime and to take caution as when opening emails and in particular annexes. Keeping used end-user software up-to-date can also prevent many problems. However, the above measures are certainly not a guarantee that an organisation will not be affected, the examples of this are known. Therefore, traps of ransomware should be primarily blocked by a functioning security solution, limited by one proper device and the possible consequences countered by a proper data redundancy solution. Paying to the causative agent of all suffering is really the last option!
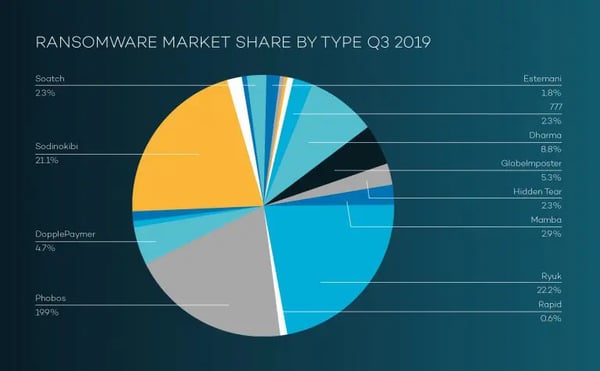
source: Coveware Q3 2019
.jpg?width=768&height=552&name=Ransomware-pie-chart2-768x552_jpg-Mar-30-2021-09-13-33-90-AM%20(1).jpg)
Ransomware protection
To realize protection against ransomware attacks, advanced threat detection is required to complement standard anti-virus software. This protection can detect and report threats at both the endpoint- and server level. Of course, something has to be done with this signalling to avoid problems. This is provided in the form of a standard (cloud) service or a 24/7 security operations center. In addition, choices are possible in operating platform so that a significantly lower risk profile arises.
Data access restriction
Access to the data is a subject that is often given limited attention from technical security aspects. It is usually focused on the content of data, or secrecy, the more legal side. Network segmentation (function or group-oriented), separate access security for critical data, prevention of single sign-on solutions across all systems, security-proof making of operating systems, these are examples of things that can already be taken into account in a standard technical design. In addition, there are functional solutions that help to manage and/or block data access and at least report..
A particular point of attention is the location, provision and coupling of the data security and backup solution. More times in recent times it has been shown that these are designed and equipped in such a way that in the case of an attack these solutions are also rendered unusable.
Quickly active after an attack
In the event of a ransomware attack (data is unreachable by encryption) an additional level of defense is necessary to ensure that the organization can quickly use the data again without being handed over to the causative agent. Multiple solutions are possible for this. Think of:
- Storage solutions such as managed snapshots and asynchronous copies of the data
- Redundantie in the backup facility including a so-called air-gap
- Use of a cloud data vault with non-mutable data storage
- In on-premise device the use of tape backup media that cannot be encrypted
These solutions apply both in (private) cloud and in on-premise environments.
Preparation is the best weapon
Drawing up a roadmap in case your organization ever falls victim to an attack is a first step to be prepared. For example, it says what the first step is in shutting down the current environment, we very data where available, how new (!) environments need to be built up, what is the correct order and priority in them is, where should it be built, how and with whom to communicate, whether AVG rules – as reporting obligation – apply. In short, it looks like a roadmap for business continuity and resiliency but with an emphasis on data security.
In addition, there is so much coming to the own management organization that a professional organization that can support at that time to get the various functional environments up-and-running again has a clear added value to limit the consequences..
Supported by professionals
Concerns about the security of data storage are well known to every IT professional. This is also a point of attention from the point of view of risk management and policy. With the approach of BPSOLUTIONS, these concerns are addressed and the right measures are taken to reduce the risks and impact. In the areas of IT advice, technical consultancy and provisioning as well as managed services, BPSOLUTIONS supports organizations with mission-critical solutions.
We also offer you the best Customer Experience with a Net Promoter Score of 87 – the extent to which customers recommend our services to others.
Would you like to know more about our solutions and services and what it can do for your organisation? Contact us on 030 303 2900 or email info@bpsolutions.com
Want to make your world a little smarter?
Get in contact with Cedric Jacott and we will reach out to you.
Related Articles
Cybersecurity & Continuïteit: Isolated Recovery Environment as a Service
27/03/2025
Cybersecurity & Continuïteit: BaaS alleen is niet genoeg
25/03/2025
Cyberaanval? De impact is groter dan je denkt
23/03/2025
Detectie en isolatie: voorbereiden op een cyberaanval
18/03/2025